The security researchers at Russian firm Positive Technologies have uncovered some truly troubling aspects of this ongoing keylogging attack campaign.
First and foremost, the attack chains all start with the exploitation of those infamous Proxy Shell vulnerabilities in Microsoft Exchange Server. We’re talking about CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207 – flaws that Microsoft patched way back in May 2021.
Successful exploitation of these vulnerabilities allows the attackers to bypass authentication, elevate their privileges, and execute remote code on the compromised Exchange servers. In other words, one of the cyber criminals dreams come true.
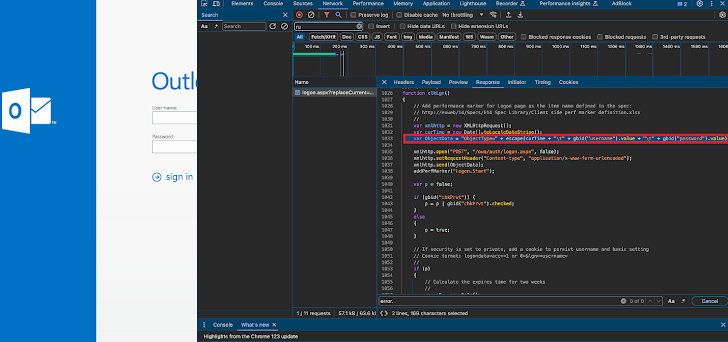
From there, the malicious actors add their keylogger to the server’s main login page, specifically the “logon.aspx” file. This allows them to capture user credentials the moment an unsuspecting victim tries to sign in.
And it gets worse – the keylogger logs these stolen credentials into a file that’s accessible from the internet. Talk about leaving the digital front door wide open!
The list of targeted organizations is equally troubling. Positive Technologies has identified victims spanning government agencies, financial institutions, IT companies, and even educational establishments. No sector seems to be off-limits for these hackers.
What’s perhaps most worrying is the wide geographic scope of this attack campaign. The researchers have traced the intrusions back to Russia, the UAE, Kuwait, Oman, and several countries in Africa, including Niger, Nigeria, Ethiopia, and Mauritius.
Want to learn deeper about the attack technically? Reach out to us and talk to an expert.
At this stage, Positive Technologies isn’t able to attribute the attacks to a known threat actor or group. But one thing is clear – these cyber criminals are well-organized, persistent, and undoubtedly hungry for more victims.
So, what can organizations do to protect themselves? First and foremost, ensure your Microsoft Exchange Servers are fully patched and up-to-date. Those Proxy Shell vulnerabilities have been exploited for over two years now – there’s simply no excuse for leaving them unaddressed.
Secondly, keep a close eye on your Exchange Server’s main login page. If you spot anything suspicious, like that “clkLgn()” function where the keylogger is injected, it’s time to sound the alarm and initiate your incident response plan.
And if the worst should happen and your organization falls victim, act fast. Identify the compromised accounts, delete the file where the stolen credentials are stored, and start the process of securing your systems and notifying affected parties. and it is always recommended to seek Cybersecurity experts help and guidance.





