Hey there, tech-savvy readers!
Imagine your data being stolen in the blink of an eye. Scary, right? Unfortunately, hackers have developed some incredibly sneaky tools that can steal your information in mere seconds. In this blog post, we’ll explore the different ways hackers can access your data and how you can protect yourself. So, buckle up and let’s dive in!
The Sneaky Tools Hackers Use
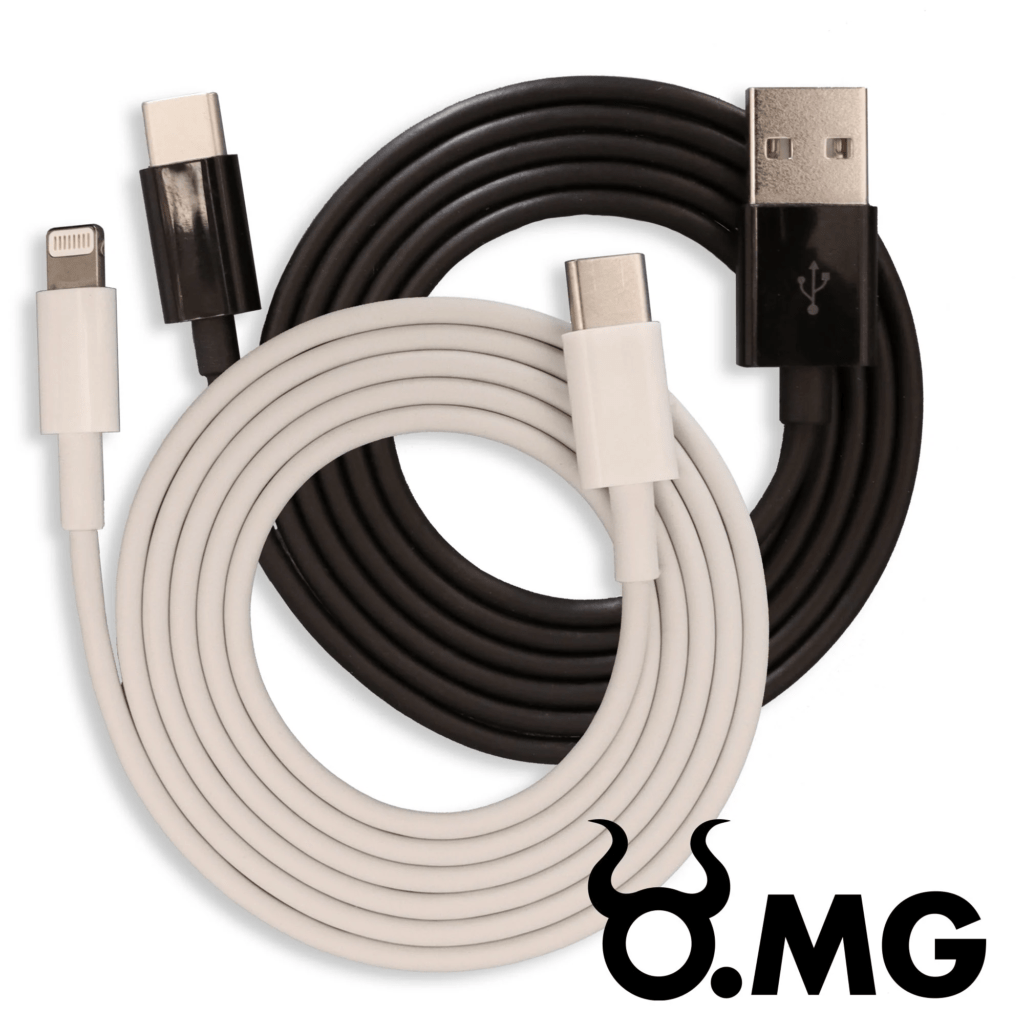
1. OMG Cable
At first glance, the OMG Cable looks like a regular charger, but it hides a tiny computer inside. Once connected to your device, it acts like a keyboard, executing commands to steal passwords, move files, and even install malware.
2. Flipper Zero
Don’t be fooled by its toy-like appearance—Flipper Zero is a powerful tool for testing infrared, RFID, and NFC. It can control devices, clone cards, capture RF signals, and much more. A hacker’s dream in a small package.

3. USB Rubber Ducky
This seemingly innocent USB flash drive is anything but. When plugged into a computer, it functions as a keyboard, executing pre-programmed keystrokes to steal data. It’s a favorite among penetration testers and hackers alike.

4. Deauther Watch
This watch might seem like a harmless gadget, but it can disconnect Wi-Fi devices from the network, causing disruptions and potential data loss. Its misuse has led to it being banned in some places.

5. LAN Turtle
A stealthy tool for remote access, network intelligence gathering, and monitoring. The LAN Turtle can be plugged into a network to provide covert access, making it a valuable tool for hackers.

6. USBKill
USBKill is designed to protect against unauthorized access by shutting down a computer when an unauthorized USB device is plugged in. However, in the wrong hands, it can be used to disrupt and steal data.

7. Wi-Fi Pineapple
The Wi-Fi Pineapple is a powerful tool for examining Wi-Fi network vulnerabilities. It allows hackers to intercept data, monitor network traffic, and launch man-in-the-middle attacks.

Protecting Yourself from Data Theft
Now that you know the tools hackers use, here are some tips to safeguard your data:
- Be Wary of Unfamiliar Devices: Avoid plugging in unknown USB drives or charging cables.
- Use Strong, Unique Passwords: Strong passwords reduce the risk of unauthorized access.
- Keep Your Software Updated: Regular updates patch security vulnerabilities.
- Enable Two-Factor Authentication (2FA): Adds an extra layer of security to your accounts.
- Monitor Network Activity: Keep an eye on unusual network traffic and unauthorized devices.
- Educate Yourself: Stay informed about the latest cybersecurity threats and best practices.
Conclusion
Hackers have developed a myriad of tools to steal data quickly and covertly. By understanding these tools and taking proactive measures, you can protect yourself and your data from falling into the wrong hands. Stay vigilant, stay secure!