Mobile devices are the center of our digital lives, they hold our conversations, finances, and even our identities. Unfortunately, that makes them prime targets for cybercriminals. A newly uncovered spyware platform, ZeroDayRAT, is raising alarms across the cybersecurity community, and for good reason: it’s not just another data-stealer. It’s a full-blown surveillance toolkit.
What Makes ZeroDayRAT Different?
Unlike typical malware that quietly harvests data, ZeroDayRAT offers attackers real-time control and monitoring of infected devices. Here’s what sets it apart:
- Cross-platform reach: Works on Android (versions 5–16) and iOS (up to version 26).
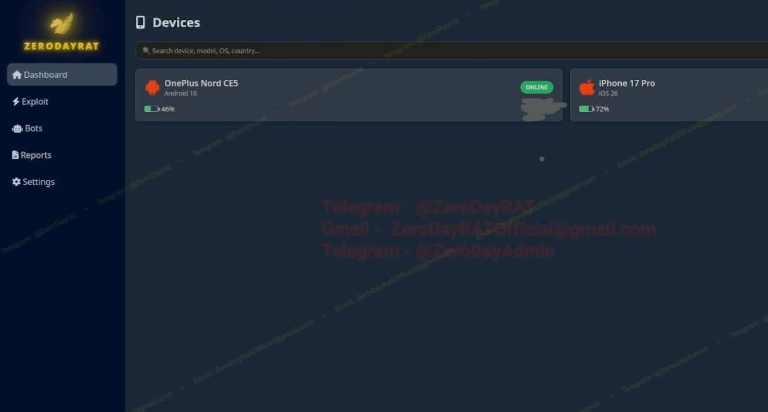
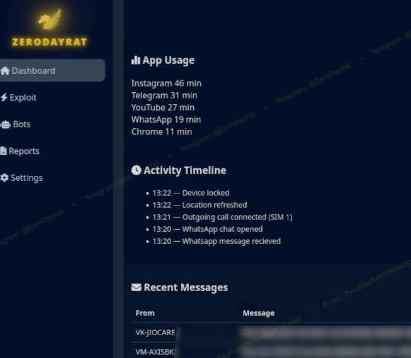
- Self-hosted control panel: Attackers get a dashboard showing device details—model, OS, battery, SIM, carrier, app usage, notifications, and even previews of SMS messages.
- Live surveillance: Real-time camera streaming and microphone feeds let attackers spy on victims as if they were in the room.
- Location tracking: GPS coordinates are plotted on Google Maps, with full history of where the victim has been.
- Account harvesting: Enumerates accounts from Google, WhatsApp, Instagram, Facebook, Telegram, Amazon, Paytm, Spotify, and more.
- Financial theft modules: Includes wallet stealers (MetaMask, Trust Wallet, Binance, Coinbase) and banking modules targeting Apple Pay, Google Pay, PayPal, and UPI-based apps like PhonePe.
In short, ZeroDayRAT is a complete mobile compromise toolkit—once the domain of nation-state actors, now sold openly on Telegram.
How It Spreads
ZeroDayRAT isn’t lurking in official app stores. Instead, it’s distributed through:
- Fake app marketplaces
- Social engineering campaigns
- Malicious droppers disguised as legitimate apps
Buyers receive a malware builder and a ready-to-deploy control panel, lowering the barrier for even low-skilled attackers to launch advanced campaigns.
Why This Matters
The rise of commercial spyware like ZeroDayRAT highlights a troubling trend:
- Lower entry barriers: Tools once requiring advanced skills are now packaged and sold like software-as-a-service.
- Persistent evolution: Attackers keep finding ways to bypass Apple and Google’s defenses, exploiting enterprise provisioning and fake updates.
- Global impact: Campaigns have already been observed across regions including Egypt, Indonesia, Iraq, Yemen, Türkiye, and India.
Related Campaigns in the Wild
ZeroDayRAT isn’t alone. Recent months have seen a surge in mobile malware:
- Arsink RAT: Uses Google Apps Script and Telegram for command-and-control, spreading via Discord and MediaFire.
- Anatsa Banking Trojan: Hidden inside a document reader app on Google Play, downloaded over 50,000 times before removal.
- deVixor Trojan: Targets Iranian users with phishing sites, includes ransomware capabilities.
- ShadowRemit Scam: Fake remittance apps trick users into bypassing regulated money transfer corridors.
- GhostChat Spyware: Distributed via romance scams in Pakistan, linked to WhatsApp hijacking campaigns.
- Phantom Click Fraud Trojans: Abuse TensorFlow.js to automate ad interactions, spreading via unofficial app stores.
- NFCShare Malware: Exploits tap-to-pay features, stealing card data via relay attacks.
Each of these campaigns demonstrates how attackers exploit trust whether in app stores, payment systems, or even personal relationships.
The Bigger Picture
Mobile malware is no longer a niche threat. It’s a mainstream cybercrime business model:
- Telegram channels act as storefronts for spyware vendors.
- Malware families evolve rapidly, mixing surveillance, fraud, and ransomware.
- Financial theft is increasingly automated, with clipboard hijacking and NFC relay attacks enabling large-scale fraud.
Protecting Yourself and Your Organization
At XEye Security, we believe awareness is the first line of defense. Here are practical steps to reduce risk:
- Stick to official app stores and avoid third-party marketplaces.
- Scrutinize app permissions—be wary of apps requesting accessibility or device admin rights.
- Enable multi-factor authentication but remain cautious of SMS-based OTPs, which malware can intercept.
- Educate employees about phishing and fake update prompts.
- Monitor device activity for unusual battery drain, data usage, or background processes.
Final Thoughts
ZeroDayRAT is a wake-up call. Mobile spyware is no longer the exclusive domain of advanced threat actors, it’s being commoditized and sold to anyone with money and malicious intent. As attackers innovate, defenders must stay vigilant, proactive, and informed.
At XEye Security, we’ll continue tracking these developments and sharing insights to help you stay one step ahead. Because in cybersecurity, knowledge isn’t just power—it’s protection.




