A newly disclosed flaw in 7‑Zip is now being actively exploited that puts countless systems and users at risk. The issue, tracked as CVE‑2025‑11001 with a severity score of 7.0, that allows attackers to execute arbitrary code remotely and could have full control on their victims devices and systems.
What’s the vulnerability?
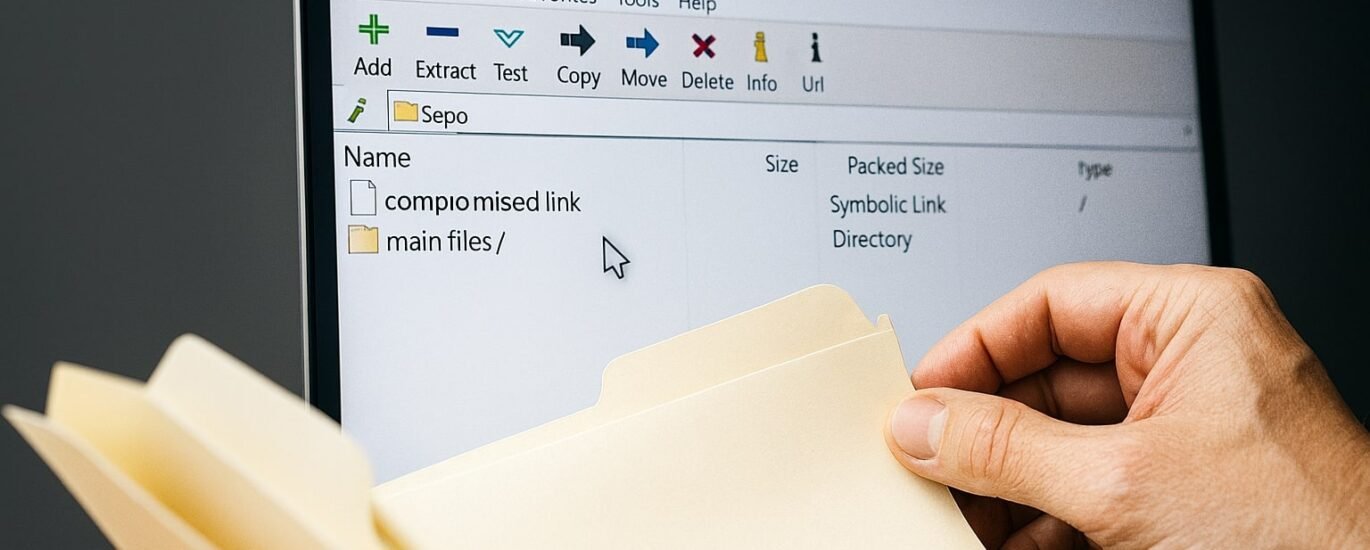
The vulnerability comes from the way 7‑Zip processes symbolic links inside ZIP archives. Normally, symbolic links are shortcuts that point to other files or directories. But in this case, attackers can create maliciously crafted ZIP files that mislead 7‑Zip into following those links outside of the intended folder structure.
Imagine opening a ZIP file that looks harmless, but behind the scenes it’s quietly redirecting the software into sensitive areas of your system. Once 7‑Zip is tricked into wandering into those unintended directories, the attacker gains an opportunity to execute code with elevated privileges. In plain terms, this means they could potentially run commands as if they were an administrator giving them far more control than they should ever have.
This flaw turns what should be a simple file‑extraction process into a dangerous backdoor, where a single careless click could expose critical parts of your system.
Why it matters
- Exploitation has already been observed in the wild.
- Proof‑of‑concept exploits are publicly available, making it easier for attackers to weaponize.
- The flaw is exploitable only on Windows systems and requires elevated accounts or developer mode enabled but that’s still a wide attack surface for enterprise environments.
What you should do
- Update immediately to 7‑Zip version 25.00 or later.
- Limit elevated account usage and disable developer mode where not required.
- Create standard user account on Windows and only use the admin privilege when needed.