Overview of CVE-2025-32756
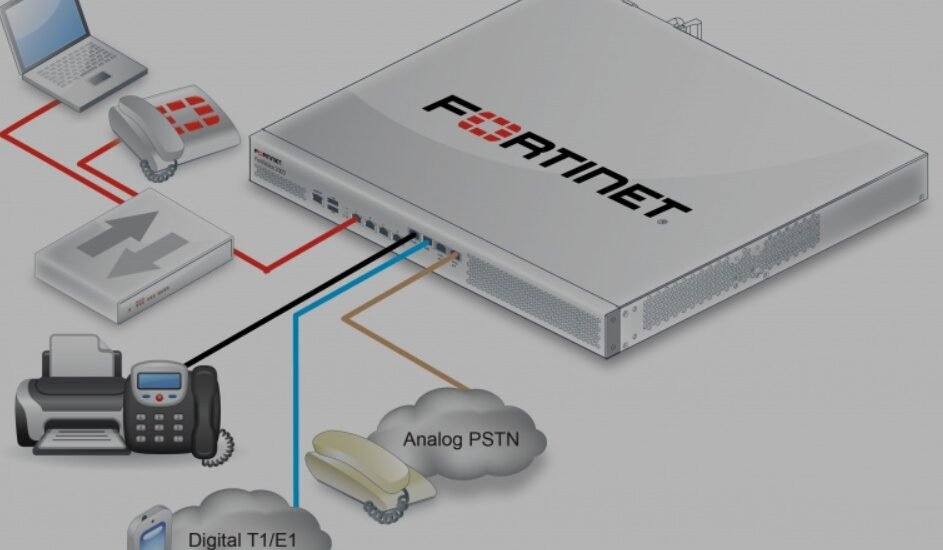
Fortinet has recently issued patches for a serious vulnerability identified as CVE-2025-32756. This security flaw is particularly concerning as it has been exploited as a zero-day vulnerability in attacks aimed at FortiVoice enterprise phone systems. With a CVSS score of 9.6 out of 10, the stakes for organizations relying on these systems are exceptionally high.
Details of the Vulnerability
The CVE-2025-32756 vulnerability is characterized as a stack-based overflow issue (CWE-121), which allows remote unauthenticated attackers to execute arbitrary commands through specially crafted HTTP requests. Fortinet has reported observing this flaw being actively exploited against FortiVoice systems but has withheld details on the scale of these attacks and the identities of the attackers.
Recommended Actions for Users
To fortify systems against potential exploitation attempts, users must promptly apply the necessary patches. Affected products include various versions of FortiVoice, FortiMail, FortiRecorder, FortiCamera, and FortiDR. If immediate patching is unfeasible, users are advised to disable the HTTP/HTTPS administrative interface temporarily. Fortinet’s security team identified the vulnerability based on malicious activity tied to specific IP addresses that were involved in the intrusion.
In conclusion, all users of relevant Fortinet products should act swiftly to mitigate the risks associated with CVE-2025-32756. Vigilance in cyber hygiene can significantly reduce exposure to such critical vulnerabilities.